DigitalSide Threat-Intel Repository
This repository contains a set of Open Source Cyber Threat Intellegence information, monstly based on malware analysis and compromised URLs, IPs and domains.
The purpose of this project is to develop and test new wayes to hunt, analyze, collect and share relevants sets of IoCs to be used by SOC/CSIRT/CERT with minimun effort.
Sharing formats [MISP] [STIX2] [CSV] [Public API] [TXT] [TAXII2] [MISP Module]
Several formats available to download the reports:
- MISP feed and events (retention: 7 days) - [GO TO]
- Structured Threat Information Expression - STIX™ v2 (retention: 7 days) - [GO TO]
- Comma Separated Values (retention: 7 days) - [GO TO]
- Public API (require apiosintDS library) - [DOCS]
- IoC lists of uniques indicators in squid like format and STIX2 (retention: 7 days) splitted in:
- TAXII2 server implementation containing STIX2 bundles shared reports (retention: 24 hours) - [GO TO]
- MISP Module available in any up to dated MISP instance [DOCS]
The majority of the informations are stored in the MISP data format. So, best way to collect data is subscribe the Digitalside-misp-feed. All sharing formats, except for STIX2.1 reports, are based on MISP export format. All reports in any format can be consumed by any up-to-dated MISP instance.
Sharing endpoints
Reports shared by two sharing endpoints:
- Github repository: you can clone, subscribe, download managing it with the power of git!
- OSINT.DigitalSide.it: You can crawl it for free and permit you to subscribe the MISP feed.
 How to subscribe the Digitalside-misp-feed
How to subscribe the Digitalside-misp-feed
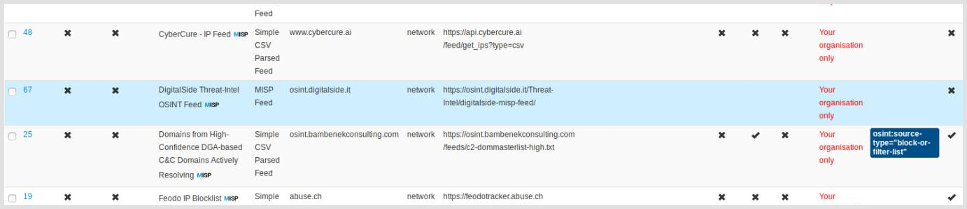
Since 2019-09-23 OSINT.digitalside.it MISP feed has been added to the "Default feeds" list availables in MISP default installation. The esasy way to subscribe the feed is select the dedicated activation button.
- Login to MISP with a user having the right permissions to manage feeds
- Go to
Sync Actions -> List Feeds -> Default feeds - Find the OSINT.digitalside.it row
- Select the row and click on "Enable selected" button at the top of the table
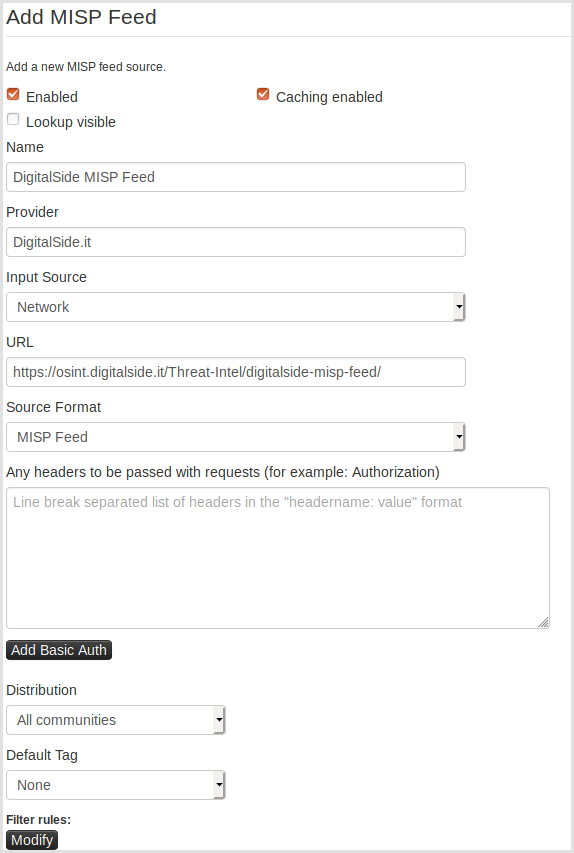
You can also subscribe the feed manually, following the below instructions.
- Login to MISP with a user having the right permissions to manage feeds
- Go to
Sync Actions -> List Feeds -> Add Feed - Add the MISP feed by using the URL https://osint.digitalside.it/Threat-Intel/digitalside-misp-feed/